Category: «General»
- The corresponding Registry file is located in c: windows system32 config. Since Windows NT 4 SP3, the SAM file is partly encrypted. The SysKey utility allows you to move the SAM encryption key off the computer and/or configure a startup password. Using the SysKey utility ^.
- Your account must be older than two days to post here. I am a bot, and this action was performed automatically. Please contact the moderators of this subreddit if you have any questions or concerns.
Jul 12, 2020 SAM file is exist under C:/Windows/System32/config in Window 7/8/8.1/10. If User want to logon on the machine, user name and password should be match for authentication entered by user. If user put wrong username and password, authentication being failed. The encryption algorithm is NTLM2 used.
Some 22 years ago, Microsoft made an attempt to make Windows more secure by adding an extra layer of protection. The SAM Lock Tool, commonly known as SYSKEY (the name of its executable file), was used to encrypt the content of the Windows Security Account Manager (SAM) database. The encryption was using a 128-bit RC4 encryption key.
The user had an option to specify a password that would protect authentication credentials of Windows accounts stored in the SAM database. If SYSKEY password was set, Windows would ask for this password during startup before displaying the login and password prompt.
While SYSKEY was not using the strongest encryption, attacking (brute-forcing or resetting) the user’s Windows login and password would not be possible without first decrypting the SAM database. As a result, a SYSKEY password would require the attacker to brute-force or reset SYSKEY protection prior to accessing the system’s Windows accounts. More importantly, an unknown SYSKEY password would prevent the user’s system from fully booting. This fact was widely exploited by ransomware and commonly abused by “tech support” scammers who locked victims out of their own computers via fake “tech support” calls.
Due to SAM database encryption, reinstalling or repairing Windows would not solve the issue unless the user had access to a recent backup or a System Restore Point. For this reason, Microsoft removed the ability to set SYSKEY passwords in Windows 10 (release 1709) and Windows Server 2016 (release 1709), steering users towards the much more secure BitLocker encryption instead. However, older systems are still susceptible to SYSKEY ransomware attacks.
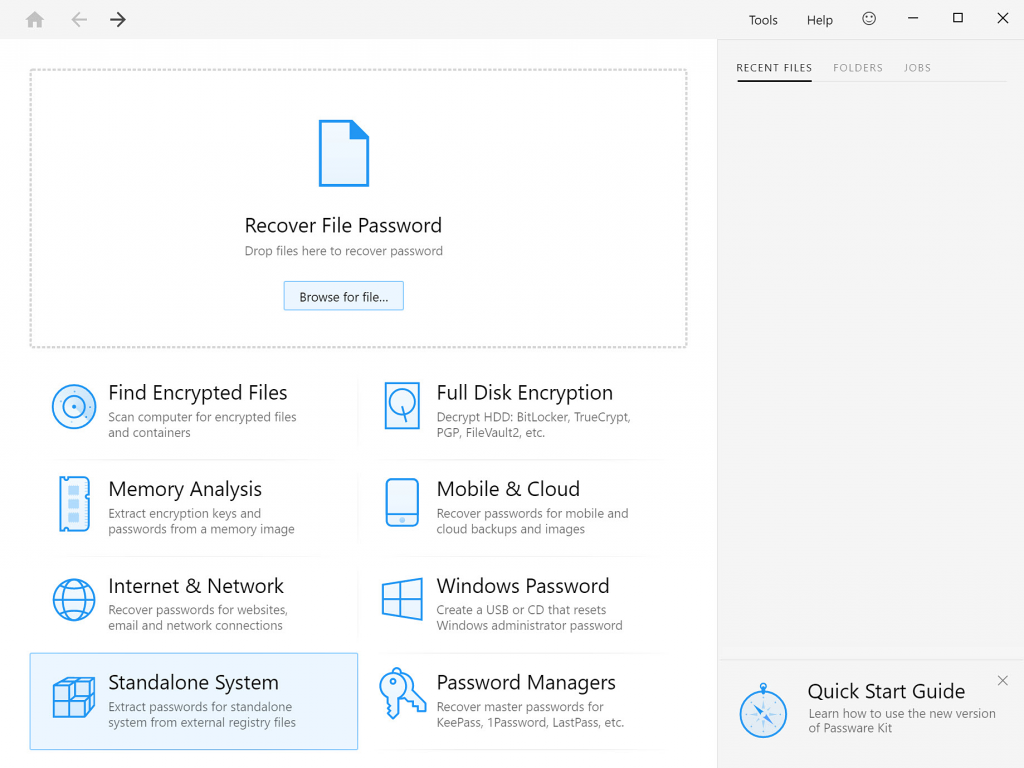
Since SYSKEY protection is fairly old by hi-tech standards, it is no longer secure (it never been in the first place). Victims of SYSKEY ransomware or “tech support” scammers can now restore their systems by recovering or resetting SYSKEY password. Elcomsoft System Recovery has the ability to discover or reset SYSKEY passwords in order to restore the system’s normal boot operation. This is also the first time ever we’re publishing screen shots of the Elcomsoft System Recovery user interface.
Removing SYSKEY Password
SYSKEY encryption is a relatively little known feature that was actively exploited by “tech support” scammers and ransomware. Once a SYSTEM password is activated, the entire SAM registry hive is encrypted. This makes it difficult to restore Windows to working condition, especially if the scammer has also removed all System Restore points. Victims of this scam will see the following message when they attempt to start their computer:
“This computer is configured to require a password in order to start up.”
Elcomsoft System Recovery can attempt to automatically reset SYSKEY protection. A straightforward removal of SYSKEY password bears the risk of breaking the Windows boot process. For this reason, Elcomsoft System Recovery performs a number of safety checks to determine whether resetting a SYSKEY password of the particular system may cause issues.
Note: instructions below assume that you already created a bootable media containing Elcomsoft System Recovery 5.40 or newer.
In order to remove an unknown SYSKEY password, do the following.

- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- In Elcomsoft System Recovery, specify the disk or partition where Windows is installed, then click Next.
- The ability to remove SYSKEY passwords is located under Miscellaneous.
- Choose SYSKEY.
- Select whether ESR should automatically search for the SAM database or specify its location.
- The tool will perform the necessary safety checks and warn you if a potential issue is detected. To just reset the password, leave the “Search…” option blank. Click “Reset SYSKEY” to finish.
- Finally, reboot your computer. Windows should start normally.
If a potential issue is discovered, you will see the following warning:
If you proceed, you will lose access to DPAPI encrypted data (EFS-encrypted files and folders). In addition, we recommend that you make backup copies of SAM, SYSTEM and SECURITY registry hives (this must be done manually).
Discovering SYSKEY Password
Cannot Decrypt Files Windows 10
Resetting the SYSKEY password may or may not work depending on configuration of the particular system. Recovering the SYSKEY password is a significantly safer operation that does not have the potential negative impact of simply resetting the password. Elcomsoft System Recovery can automatically check your computer to look up for cached SYSKEY passwords throughout the system. The tool will analyze various registry keys, temporary files and databases to look up for a cached copy of SYSKEY password. If this is successful, SYSKEY protection can be removed instantly and risk-free.
In order to look up for SYSKEY password, do the following:
- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- Follow steps 2 through 6 in Elcomsoft System Recovery. However, this time make sure the “Search for SYSKEY plain text password” option is selected.
- You will have the choice between a fast or thorough scan. Tap Recover SYSKEY to continue. The tool will attempt to locate the SYSKEY password on your computer.
- Take a note of the discovered SYSKEY password and reboot your computer. Enter the discovered SYSKEY password when prompted.
The Cipher.exe command line tool was originally released with Windows 2000, commensurate with the release of NTFS V5.0 and the ability to use the Encrypting File System (EFS). Microsoft continues to upgrade the tool as Windows Operating System security solutions evolve. With the release of Windows 7, the Cipher command becomes a critical component of desktop support.
Most technical support sites and blogs reference use of the Cipher tool to “wipe data from your disk”. While the description is not entirely accurate, the cipher tool can be used to modify the binary content for a designated structure of the hard drive, effectively making it indecipherable. The syntax for this effort is:
Cipher /w:c:usersuser1 would scramble the bits for everything within the usersuser1 directory making it unusable. The solution was designed to scramble the bits within a deleted folder, preventing its recovery, though it could be used to disable an entire directory structure or drive if not used with caution.
Cipher can also be used to encrypt files or folders using the /E option (combined with the /S option for recursive encryption of folders and subfolders). Decryption requires the /D switch. Both switches implement the EFS functionality of NTFS.
Cipher switches added from Windows XP through Windows 7, become essential to the management of security features associated with current OS deployment and operation.
Microsoft Technet provides a table containing the basic Cipher switches. Jack Cobben, Jack’s Server Blog created a straight forward overview while preparing for the Windows 7 MCTS 70-680 exam.
Creation of a recovery agent, for instance, is essential to the management of encrypting file system (EFS), Bitlocker, and other digitally certified features. The /R: switch is mentioned as a means to generate a new recovery agent certificate and private key for your system. If this switch is used, all other switches are ignored, suggesting its relevance. Unfortunately the reason and ramifications are not explained well.
Pay close attention to the following paragraphs. I really wanted to bold and italic that last sentence. Really. Pay attention.

Prior to the development of the Credential Manager, a key Windows Vista and Windows 7 element, the File Encryption Key (FEK) associated with an EFS file was stored in the Security Account Manager. Hacker tools were available to recover a FEK from the SAM. If an administrator took ownership of an encrypted file, with a little effort, they could retrieve the FEK from the SAM and recover the encrypted file. When EFS is used to encrypt a file in Windows 7, the FEK is stored within the encrypting user’s Digital Certificate. If a Digital Certificate does not exist for the user, a public-private key pair and certificate are generated for the user, the FEK is added, and the certificate is stored in the local Windows 7 Credential Manager. The entire process is transparent to the user. To protect the integrity of the PKI model, only the owner of the certificate can export the FEK, or their public key, or their private key, or permissions to access the file. Not even a local or domain administrative account can take ownership, export the FEK, or export a user’s credential.
In order to protect enterprise assets, Microsoft created the concept of a recovery agent. The recovery agent is a pre-defined, public-private key pair and certificate designated to hold any FEK’s created on the system. This effectively grants the administrative owner of the recovery agent the ability to recover an encrypted file. If you don’t create a recovery agent before encrypting any files there is no administrative storage location for the FEK and only the encrypting user has the FEK. Similarly, if the file owner/encrypting user grants file permission to someone who does not have a locally stored digital certificate, NTFS security permissions will be granted BUT there will be no storage location to replicate the FEK and the user granted (or an administrator taking ownership) permissions will be unable to access the encrypted file. For the sake of safety and recovery, you really must have a recovery agent installed on each system. Alternately, Active Directory Certificate integration may be enabled in a domain environment, and group policy can be used to present a recovery agent credential to computers within the domain. But recovery agents only resolve a portion of the encrypted file management and recovery scenario.
To fully maintain the integrity of the PKI model, only the user of a specific credential can export or make a copy of their credential information. Backup solutions will copy encrypted files, but will not copy the Credential Manager content. Migration tools like Windows Easy Transfer (WET) and the User State Migration Tool (USMT) can be configured to capture encrypted files from a source system, and to restore them to a target system. The only method to transfer a user’s credential is for the user to export their own public-private key pair to a folder that will be backed-up or transferred prior to the capture or transfer process. Failing to export the credential, relocate it to the new system, and import it into the new local credential manager can be catastrophic. The outcome – encrypted files are relocated but cannot be decrypted because the FEK (contained within the secured certificate) was not transferred. Recovering a system image that lacks the exported digital certificates will mean that any encrypted data is inaccessible even to the user who originally encrypted the file.
Microsoft provides a great Technet article that incorporates the steps using USMT components to migrate encrypted files. The article provides details for using the MMC Certificate snap-in and export wizard – a sequence which few standard users will be able to follow – for a user to export their own certificate prior to use of WET or USMT. Viable for the technically savvy user, though of little value in a Lite-touch or Zero-touch migration scenario. It would be better to show users how to enter the Credential Manager from the Control Panel and merely select the Back Up Vault link.
For automated sequences, Cipher may come to the rescue. The /X: switch is referenced in the Technet article above, although with minimal definition and no example. A search of the Microsoft Command Line reference for Cipher drops all the way back to Windows XP and does not mention the /X: switch at all.
Using an elevated command prompt and typing Cipher /? Yields the following for the /X: switch.
| X | Backup EFS certificate and keys into file filename. If efsfile is provided, the current user's certificate(s) used to encrypt the file will be backed up. Otherwise, the user's current EFS certificate and keys will be backed up. |
The syntax is either
In the first instance you export the entire user credential file, in the latter you export only a credential and the FEK for the file specified. This is useful to export the FEK and credentials for EFS encrypted files, without exporting the entire credential vault that includes server and trust authority credentials. If you do not want user interaction, you will also need to prepare a script that, in order,
- Confirms the request
- Identifies a password to protect your exported .pfx file (containing both public and private keys as well as the FEK).
- Confirm the password via a second, identical entry.
The process creates a file called exportfilename.PFX in the root of the designated user’s profile that can then be exported or copied.
Submitting a command sequence for user execution or forcing a login script will assure that the user has exported their credentials prior to the execution of any backup or migration sequence. The drawback will be the potential exposure of the password protecting the credential file if the command script is captured.
You may also choose to explore the /REKEY and /R switches. These will allow you to reset the key or create a recovery agent for files rather than focusing on the export of individual certificates.
If you are familiar with Powershell, head straight to Posh Tips for examples incorporating Export-PSCredential and Import-PSCredential functions. These provide a more sophisticated and comprehensive credential vault export and import feature.
For more detailed information regarding certificate based EFS, recovery keys, enabling and disabling EFS, exporting and importing keys, and best practices refer to the Microsoft Small Business Security Guidance article. Although the screen shots and context pre-date Windows 7, the material remains relevant toward understanding encryption migration and recovery.
Enjoy,
Steven Fullmer
Interface Technical Training Staff Instructor
You May Also Like
Decrypt File Tool
TagsDecrypt Sam File Windows 7 32 Bit
.PFX, Cipher, Cipher.exe, EFS, Encrypting File System, FEK, File Encryption Key, NTSF, Win 7, Windows 7